Sunday, July 31, 2011
Friday, July 22, 2011
Create hard to crack passwords with Cyberx Password Generator
Free Password Generator Tool
Cyberx Password Generator is an easy to use password generator program available for install or portable, the software can create random and pronounceable passwords that are very difficult to brute force(cracking a password using dictionary words). Some websites let you create hard to guess passwords online but they could be intercepted in the process, creating a password using a website it is not a security good idea. This free open source password generator works offline, it can be sent to your Windows taskbar and launched with a single click when you need it.
Cyberx Password Generator is an easy to use password generator program available for install or portable, the software can create random and pronounceable passwords that are very difficult to brute force(cracking a password using dictionary words). Some websites let you create hard to guess passwords online but they could be intercepted in the process, creating a password using a website it is not a security good idea. This free open source password generator works offline, it can be sent to your Windows taskbar and launched with a single click when you need it.
The password generator settings allow for great customization, they can be set to predispose certain prefix and/or suffix, specify password length, which can be of in between 1 and 1028 characters, specify if numbers and special characters can be used (some sites don’t allow them), and excluding of characters that are similar, you might want to get rid of the letter O and number zero when creating a password as they often lead to confusion
Once you have created your password or a list of passwords of up to a thousand contained in a single list, you can export them as .txt, .htm, .csv or .xml, copy the password to the clipboard to be used straight away, or copy the SHA1 and MD5 hash values instead. The password details window will let you know the entropy of the password in bits and a coloured bar will indicate its strength, you also get the hash values of your password.
Cyberx is user friendly and a good alternative to diceware, a crude way to create random passwords using dices, the help file is only available in Italian online, but this is not a big issue, if you get lost just creating a password click on the “i” icon next to each box and an informative help window will popup telling you what each settings box is for.
Thursday, July 14, 2011
Remove-Regsvrexe-And-New-Folder.exe
Plug a pendrive into a public computer and you will be pesked by the continuously replicating “New Folder.exe” virus or  the “regsvr.exe” virus. Hear my story, while I transferred my notes last night (around 600 folders) and I was surprised to see that around 450 MB of space was eaten by these self replicating space eaters ! I was runningLinux so these were not a concern for me, but when I plugged my pendrive into my virtual machine (windows xp sp3), it caused multiple problems of explorer corruption and disabling registrytools.
the “regsvr.exe” virus. Hear my story, while I transferred my notes last night (around 600 folders) and I was surprised to see that around 450 MB of space was eaten by these self replicating space eaters ! I was runningLinux so these were not a concern for me, but when I plugged my pendrive into my virtual machine (windows xp sp3), it caused multiple problems of explorer corruption and disabling registrytools.
 the “regsvr.exe” virus. Hear my story, while I transferred my notes last night (around 600 folders) and I was surprised to see that around 450 MB of space was eaten by these self replicating space eaters ! I was runningLinux so these were not a concern for me, but when I plugged my pendrive into my virtual machine (windows xp sp3), it caused multiple problems of explorer corruption and disabling registrytools.
the “regsvr.exe” virus. Hear my story, while I transferred my notes last night (around 600 folders) and I was surprised to see that around 450 MB of space was eaten by these self replicating space eaters ! I was runningLinux so these were not a concern for me, but when I plugged my pendrive into my virtual machine (windows xp sp3), it caused multiple problems of explorer corruption and disabling registrytools.
Time for some virus busting I guess..here is how you can remove “regsvr.exe” and “new folder.exe” from your computer.
Step 1 - Some Startup Repairs
First of all, boot into safe mode.After you get to your desktop,press F3 or Ctrl + F and search for “autorun.inf” file in your computer and delete all the subsequent files. I case you are no able to delete them, select all the files and uncheck the”Read Only” option. If you are still not able to delete them , you might want to try out Unlocker tool to delete the files.
Now go to
start – > run –> type ”msconfig”
and press enter
Go to startup tab and uncheck “regsvr”, click ok and then click on “Exit without restart”.
Now go to
control panel –> scheduled tasks and delete “At1” task listed there.
Once done, close all windows.
Step 2 - Changing Configurations
Your registry might be disabled,and you need to activate it back to undo all the malicious changes done by worm.In order to do that, you need to go to
start – > run –> type ”gpedit.msc”
and press enter
then navigate to
users configuration –> Administrative templates –> systems
Find “prevent access to registry editing tools” , double click it and change the option todisable.
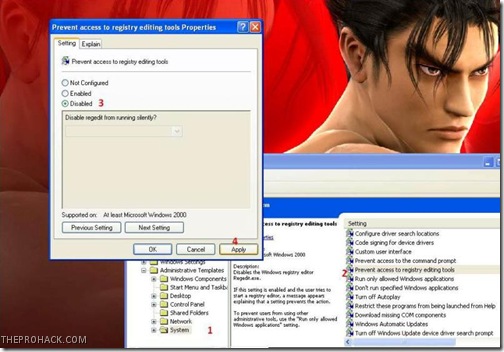
Once done, your Regedit will be enabled. In case your task manager is disabled, you need to enable it.
Step 3 - Registry Edits
Now we have to perform some registry edits to enable our explorer and to remove all instances of worm from the registry. Go to
start – > run –> type ”regedit”
and press enter
Click on Edit –> Find and search for regsvr.exe . Find and delete all the occurrences ofregsvr.exe virus (don't delete regsvr32.exe as its not a virus).
then navigate to entry
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
and modify the entry
Shell = “Explorer.exe regsvr.exe”
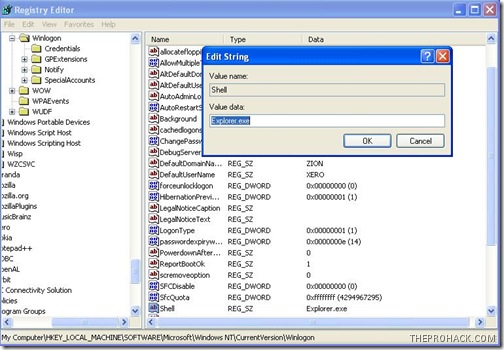
to delete the regsvr.exe from it,so that it becomes
Shell = “Explorer.exe”
Once done, close all windows and get ready to delete all virus files.
Step 4 - Deleting Virus Files
The final step is to delete all the virus files in your computer. To do this, Press F3 or Ctrl + F and search for regsvr.exe (make sure to search in hidden folders ) and delete all “regsvr.exe” “svchost .exe” files (notice the gap between ‘svchost’ and ‘.exe’, keep in mind you don't delete the legitimate file.).
Clean your recycle bin and restart your PC (perform a cold boot).
Volia..you have cleaned your computer from regsvr..just make sure to scan your pendrive the next time you plug in :)
Monday, July 11, 2011
Nokia mobile Unlock Code Generator v3.10
Nokia Mobile Unlock code generator unlocks the Nokia cell phones and help us to use any service provider we want. This application will generate network unlock codes for your mobile phone which you simply enter into the phone keypad to unlock your phone to all networks.
Nokia Free unlock codes calculator allow users to use their mobile phone with any service provider around the world.
It helps in Repairing, removing SIM restrictions and unlocking Nokia, Samsung, Siemens, Maxon, NEC, Sony, Panasonic, Vitel, AEG / Telital, Alcatel cellphones.
How to use Nokia mobile Unlock code generator:
1. Remove your sim card and switch on the phone.
2. Type *#06# to get phone serial number and enter this into the program along with your phone model number and current network.
3. Extract and Install the Nokia Phone manager. The click on Nokia Free Unlock.exe(by defaultC:\Program Files\NokiaFREE Unlock Codes Calculator) to start it.
4. Now select your Mobile model(If not found select DCT2 or DCT3 or DCT4 accordingly).
5. Now Enter your IMEI number in the IMEI box.
6. Click on calculate button and you will receive a list of unlock codes
(I usually find that either the first or last code works fine)
7. Now you have the list of codes, enter the code into your phone (use the * key for the pw+ characters)
8. Your phone will say something like 'sim restrictions lifted' and then reboot itself
That's it you can now use any sim card in your phone.
(I usually find that either the first or last code works fine)
7. Now you have the list of codes, enter the code into your phone (use the * key for the pw+ characters)
8. Your phone will say something like 'sim restrictions lifted' and then reboot itself
That's it you can now use any sim card in your phone.
Thursday, July 7, 2011
Top 5 Best Black Hat Hackers
 We all are fond of learning about hacking and hackers so today in this post HPH is presenting the top 5 worlds famous and best black hat hackers. The hackers in this list are not only one of the best but they helped(indirectly) a lot to make the computer and internet security better and left their own mark. To know about these great hackers continue reading this post.
We all are fond of learning about hacking and hackers so today in this post HPH is presenting the top 5 worlds famous and best black hat hackers. The hackers in this list are not only one of the best but they helped(indirectly) a lot to make the computer and internet security better and left their own mark. To know about these great hackers continue reading this post.
Related: What is Hacking and Hacker.
Kevin Mitnick
 Kevin Mitnick is a very intelligent hacker of his own style calledSocial Engineering. He used this technique at the age of 12 to bypass the punchcard system used in the Los Angeles bus station. He hacked the first computer network at the age of 16 and copied the valuable software of Digital Equipment Corporationfor which he is sentenced for 12 months followed by supervise release. Mitnick used his social engineering technique to hack computer networks, email, coping most valuable software's etc.., which made him a most wanted cyber criminal in the history of USA. After getting caught by US government he changed attitude and now he is a best computer security consultant.
Kevin Mitnick is a very intelligent hacker of his own style calledSocial Engineering. He used this technique at the age of 12 to bypass the punchcard system used in the Los Angeles bus station. He hacked the first computer network at the age of 16 and copied the valuable software of Digital Equipment Corporationfor which he is sentenced for 12 months followed by supervise release. Mitnick used his social engineering technique to hack computer networks, email, coping most valuable software's etc.., which made him a most wanted cyber criminal in the history of USA. After getting caught by US government he changed attitude and now he is a best computer security consultant. Robert Morris
 He is the founder of buffer overflow attacks and the first computer worm in internet which is named Morris Worm, not only that but he is also a co-founder od ViaWeb(Now it is called asYahoo! Store) which is the first web-based application which lets users to create their own online store with very little effort and less expertise. According to Morris the worm created by him is intended to gauge the size of internet, but when it comes to real the worm has the capable to find the vulnerability's of the targeted systems and which in turn gives access to hackers by exploiting the security hole.
He is the founder of buffer overflow attacks and the first computer worm in internet which is named Morris Worm, not only that but he is also a co-founder od ViaWeb(Now it is called asYahoo! Store) which is the first web-based application which lets users to create their own online store with very little effort and less expertise. According to Morris the worm created by him is intended to gauge the size of internet, but when it comes to real the worm has the capable to find the vulnerability's of the targeted systems and which in turn gives access to hackers by exploiting the security hole. The creation of this worm made him the first person to be prosecuted and convicted in US under the Computer Fraud and Abuse Act and sentenced for 3years of prohibition, 400hours of community service, $10,050 fine and his supervision costs.
After this he has achieved many things like being a cofounder of ViaWeb which was sold to yahoo for $48million, Receiving a Ph.D in Applied science by Harvard, being a professor in MIT(Massachusetts Institute of Technology) and so on which made him special in this world.
Loyd Blankenship(a.k.a +++The Mentor+++)
Loyd Blankenship is well know as The Mentor and written as +++The Mentor+++, In 1970s he is a well-known hacker and writer and is also very very famous for his The Hackers Manifestoand was published in the underground hacker ezine Phrack and you can read it from here. Loyd gave a reading of The Hacker Manifesto and offered additional insight at H2K2. (Source: Wikipedia - http://en.wikipedia.org/wiki/Loyd_Blankenship)
Jonathan James(a.k.a c0mrade)
Jonathan was the first juvenile to be sent to sentence at the age of 16. Jonathan is well known for his high rated intrusions including gaining access to DTRA(Defence Threat Reduction Agencies) servers and installing a backdoor which in-turn gave him access to sensitive email and passwords of their employees and 10 other military systems.
The other major intrusion is breaking in to NASA servers and stealing the software(Actually it is a source code) worth of $1.7 Million, This intrusion forced NASA to shutdown their systems for 4 weeks to find and fix the problem. The software that was steeled by J.J is used to support the physical environment in International Space Station.
The other major intrusion is breaking in to NASA servers and stealing the software(Actually it is a source code) worth of $1.7 Million, This intrusion forced NASA to shutdown their systems for 4 weeks to find and fix the problem. The software that was steeled by J.J is used to support the physical environment in International Space Station.
J.J was died in May 18, 2008 by committing a suicide.
Kevin Poulsen(a.k.a Dark Dante)
Kevin Poulsen is also the most wanted and the best hacker once is US, Kevin is well known for his take over of all the telephone lines of Los Angeles Radio Station(KIIS-FM) by which he would be the guaranteed 102nd caller for which he will win the prize of a Porsche 944 S2. Later that when FBI started perusing him he went underground. When he was underground, the famous NBC featured a show called Unsolved Mysteries, at that time their 1-800 telephone lines are mysteriously crashed…. Later that incident Kevin was arrested for his actions and was sentenced for 51 months in prison and ordered to pay $56,000.
After this Kevin restarted his career as a journalist and started writing about the security. Later after some time he resigned for his journalist post and started to be a freelance writer and now he’s a senior writer for Weird News.
article source:hoverpchacks
Monday, July 4, 2011
3 Ways To Choose A WPA Key That’s Difficult To Hack
Wi-Fi is a
great way to stay connected to the Internet all over your home without huge
wires, and is the only way many devices like the IPad have access to the
Internet. Too often users compromise security for convenience and either leave
their network open or choose an easy password. Here are three tips to choosing
a secure WPA key for your home Wi-Fi network
2. Use Random Capitalization
Since most things are case sensitive getting into the habit of a capitalization pattern goes a long way to creating an unhackable network key. For example, On AnD oFf capitalization is one way to almost guarantee they wont be able to gain access without permission.
3. Double Up Numbers
Using numbers and letters is another great basic tip but a truly random string of numbers is hard to remember but using something like a birthday leaves you vulnerable to anyone who knows personal info about you. One happy medium is to double or triple up numbers. For example, if your birthday is 12/10/1980 than instead of using 12101980 as part of the password use 1212101019801980 it will be far harder to guess and super easy to remember.
Saturday, July 2, 2011
Google boosts Gmail's anti-phishing Filters
Google this week added an anti-phishing feature to Gmail that automatically displays the sender's address for some messages.
The move is designed to help users spot suspicious messages that try to dupe people into divulging their Gmail log-in credentials or other personal information.
Starting Tuesday, Gmail began showing the sender's email address on all messages from people the recipient had either not sent mail to or were not in his contact list. Additionally, messages sent via a third-party firm -- such as an email marketing bulk mailer, which are often used by retailers to blast out deals -- now automatically display the sending address.
"If someone fakes a message from a sender that you trust, like your bank, you can more easily see that the message is not really from where it says it's from," said Google software engineer Ela Iwaszkiewicz in a post to the company's Gmail blog on Tuesday.
Previously, Gmail users could expose the sender's address by manually clicking on a "show details" link in the email service's interface.
Google published more detail on the new anti-phishing feature on the Gmail support site.
According to that page, Gmail will stop showing the full address of a sender once the recipient communicates with the sender, either by replying to emails or adding the address to Gmail's contact list.
Google uses the message header to uncover the sender's email address, and whether the message was transmitted via a third-party domain.
Other Web mail services lack a similar feature. Microsoft's Hotmail, for instance, will display the sender's address at the user's command, but does not do so automatically. In Hotmail's case, hovering the mouse over the sender's name displays a pop-up that shows the full address.
Google has acknowledged several aggressive phishing attacks aimed at Gmail users, most recently earlier this month when it accused Chinese hackers of running a months-long campaign to hijack the accounts of senior U.S. and South Korean government officials, military personnel, Chinese activists and journalists.
Hackers had sent spoofed email messages purportedly from friends or colleagues that included a link to a fake Gmail login page, which the criminals used to collect usernames and passwords.
China denied that its government was responsible for the attacks.
Data breaches at a host of high-profile companies, from the mass mailer Epsilon to Sony, have also revealed millions of email addresses this year, and put ammunition for targeted phishing attacks -- called "spear phishing" -- in hackers' hands.
Subscribe to:
Posts (Atom)

